MPLS VPNs are connectionless. MPLS seperates traffic and provides privacy without the need for Layer 2 tunneling protocols and encryption. This eliminates significant complexity during the provisioning process.
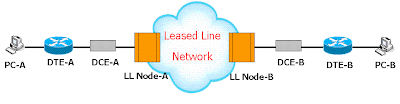
MPLS solves the scalability issues encountered by Frame Relay and ATM deployments by allowing service providers to provision multiple VPNs for multiple customers without the chore of provisioning tens to hundreds of virtual circuits for each and every closed user group or customer. An example of an MPLS VPN is shown in the picture below. Customers A and B share the service provider infrastructure while having the ability to form their own closed user groups with utmost security. They also can run their own routing protocols.

The MPLS model requires the CPE routers to directly exchange routing information with provider edge routers, as opposed to exchanging routing information with all other CPE routers that are members of the VPN. Members of the VPN are identified as belonging to the closed user group by means of labels. These labels carry next-hop information, service attributes, and a VPN identifier, which keeps communications within a VPN private.
At the ingress into the provider network, incoming packets from the CPE router are processed, and labels are assigned based on the physical interface these packets were received from. Labels are applied using VRF (VPN Routing and Forwarding) tables. The forwarding tables are predetermined, and incoming packets are examined only at the ingress LSR. The core devices or Provider (P) LSRs merely forward these packets based on labels.
Reference :
“Advanced MPLS Design and Implementation”, Vivek Alwayn, Cisco Press, 2002.




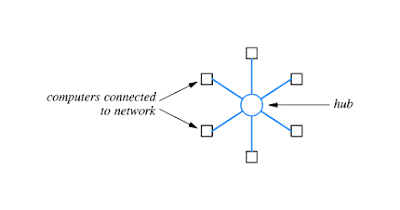 A network uses a star topology if all computers attach to a central point.
A network uses a star topology if all computers attach to a central point. A network that uses a ring topology arranges for computers to be connected in a closed loop. The name ring arises because one can imagine the computers and the cables connecting them arranged in a circle.
A network that uses a ring topology arranges for computers to be connected in a closed loop. The name ring arises because one can imagine the computers and the cables connecting them arranged in a circle. A network that uses a bus topology usually consists of a single, long cable to which computers attach. Any computer attached to a bus can send a signal down the cable, and all computers receive the signal. Because all computers attached to the cable can sense an electrical signal, any computer can send data to any other computer. Of course, the computers attached to a bus network must coordinate to ensure that only one computer sends a signal at any time or chaos results.
A network that uses a bus topology usually consists of a single, long cable to which computers attach. Any computer attached to a bus can send a signal down the cable, and all computers receive the signal. Because all computers attached to the cable can sense an electrical signal, any computer can send data to any other computer. Of course, the computers attached to a bus network must coordinate to ensure that only one computer sends a signal at any time or chaos results.